1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
| ┌──(root㉿kali)-[/home/ace]
└─
┌──(root㉿kali)-[/home/ace]
└─
┌──(root㉿kali)-[/home/ace]
└─
┌──(root㉿kali)-[/home/ace]
└─
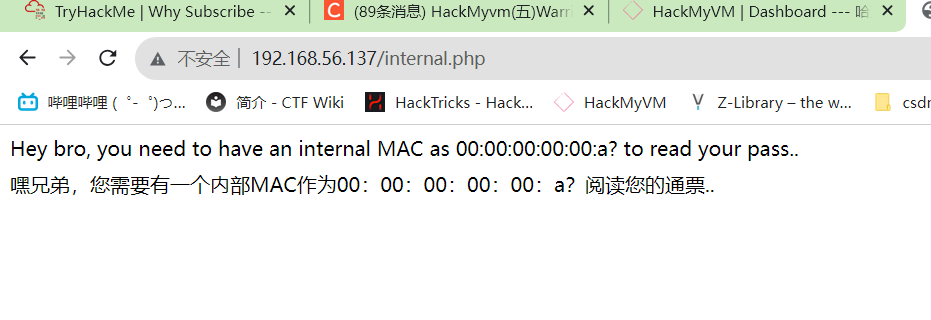
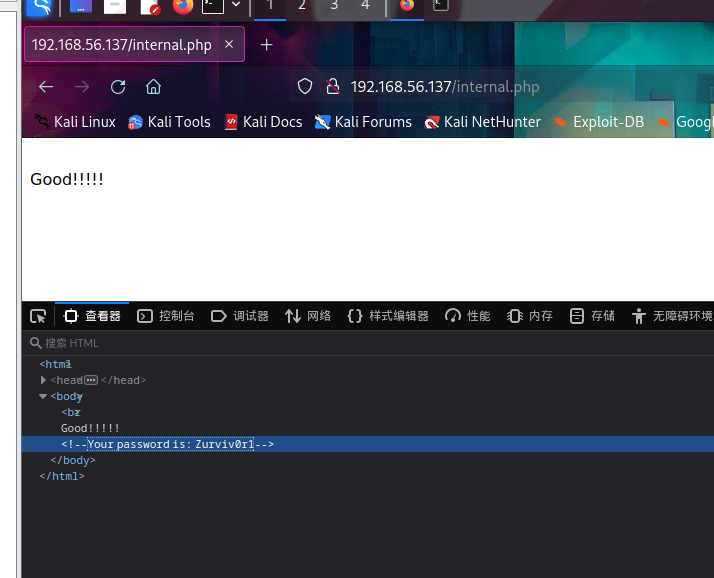
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.181.139 netmask 255.255.255.0 broadcast 192.168.181.255
inet6 fe80::20c:29ff:fe4d:2f0b prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:4d:2f:0b txqueuelen 1000 (Ethernet)
RX packets 45603 bytes 6896380 (6.5 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 43194 bytes 2636881 (2.5 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.56.127 netmask 255.255.255.0 broadcast 192.168.56.255
inet6 fe80::200:ff:fe00:af prefixlen 64 scopeid 0x20<link>
ether 00:00:00:00:00:af txqueuelen 1000 (Ethernet)
RX packets 561753 bytes 176917710 (168.7 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 549265 bytes 80914874 (77.1 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 4 bytes 240 (240.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4 bytes 240 (240.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
|